Here’s why we think there is something interesting about the “Beyond the Grave Virus” supposedly affecting hedge funds. We were curious because there was some chatter about it being a hoax. While this can be (very) true, we think it was worth looking in to. Who knows, it may possibly be an early exploration expedition and the beginning of something material to come. Since there is no conclusive data, this is merely some high-level analysis done to piece together some of the information we found. We wanted to provide some general info and also wanted to provide a starting point for anyone else as curious as us to conduct this research.
Naturally the first thing we did because there wasn’t much information to go on is to look at the domain name associated with this particular event. In doing so, we found that the aksia[dot]co domain name was registered a little less than three months ago on December 4th 2018. It was registered at gandi.net a popular registrar in France.
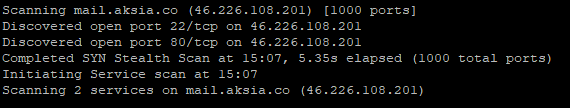
We searched for dns records and found that the ‘A’ record pointed to IP address 46.226.108.201. A quick scan of the server showed there were two ports open, SSH port 22 and HTTP port 80. These are pretty common ports found on webservers in hosted environments. It is also common to see these ports used in command and control servers.
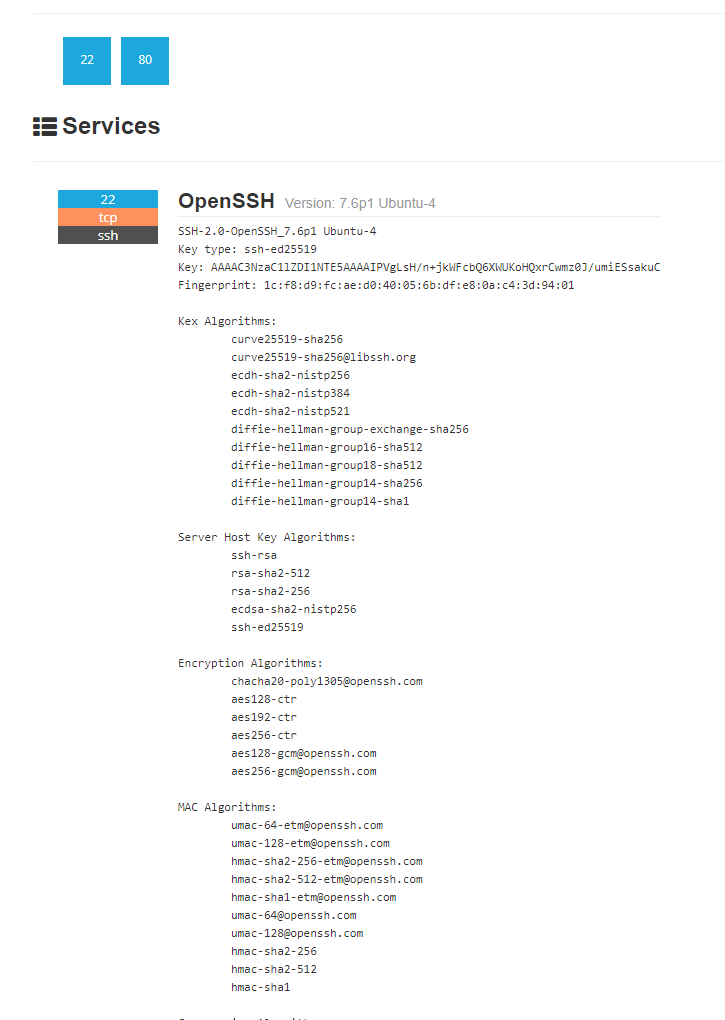
A search on shodan also listed these ports as open and identified that a particular distribution and version of *.nix was running on that machine.
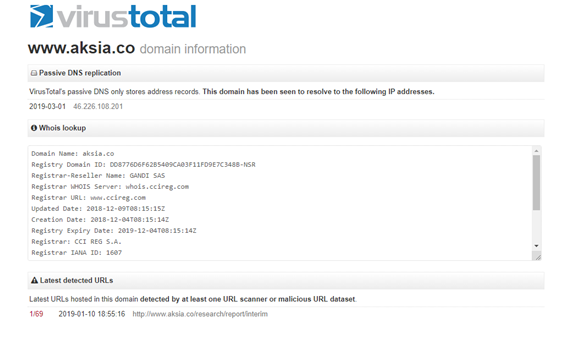
Firstly, IP address 46.226.108.201 was found to be hosting the url http[:]//www[dot]aksia[dot]co/research/report/interim that was detected to be a malicious site by only one url scanner. You can browse that here: https://www.virustotal.com/en/domain/www.aksia.co/information/ or view the image below.
We conducted some further analysis to find other domains associated with the IP address and came across the domain milos[dot]whoswho (great tld, isn’t it?)
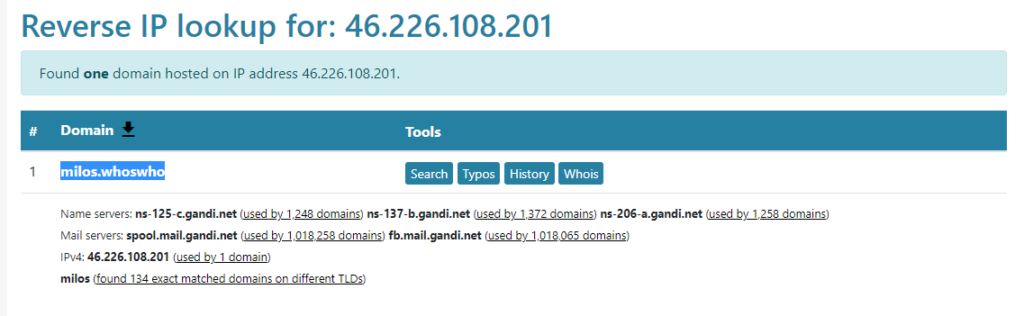
When searching for IP addresses associated with milos[dot]whoswho we found that virustotal had a couple of interesting items, specifically IP address 217.70.184.38. IP address 217.144.28.210 also had one interesting item but not as interesting as the other IP.
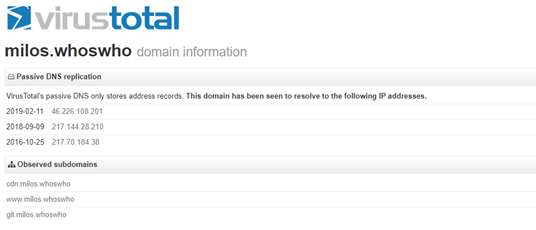
Th IP address 217.244.28.210 was associated with the domains below. virustotal listed a file that was analyzed back in March 2015 for this IP. It was found to contain malicious content on 48 of the 56 listed URL scanners.
- 2019-03-01 www[dot]milospolakovic[dot]sk
- 2019-03-01 milospolakovic[dot]sk
- 2018-09-09 milos[dot]whoswho
- 2018-07-23 www[dot]milos[dot]whoswho
- 2018-06-21 git[dot]milos[dot]whoswho
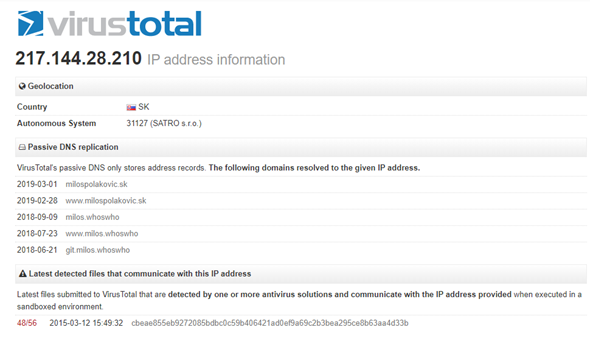
We then moved on to 217.70.184.38 and further enumerated this IP to find some interesting items. First of all, this one IP address has over 425,000 domain names associated with it. If you’re running a hosted server its common to see hundreds, sometimes thousands of domain names associated with an IP address, but not over 425,000 addresses. That’s simply mind-boggling.
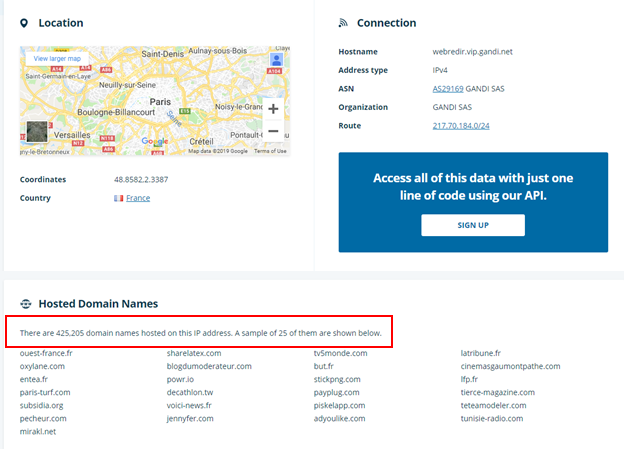
A search on virustotal showed that IP 217.70.184.38, had several (we didn’t have enough screen real estate to take a full screenshot so we broke them up) malicious files that were downloaded from this IP and several files that communicated back to this IP indicating that it could have served as a command and control server (also possibly part of a botnet). You can view it here: https://www.virustotal.com/en/ip-address/217.70.184.38/information/
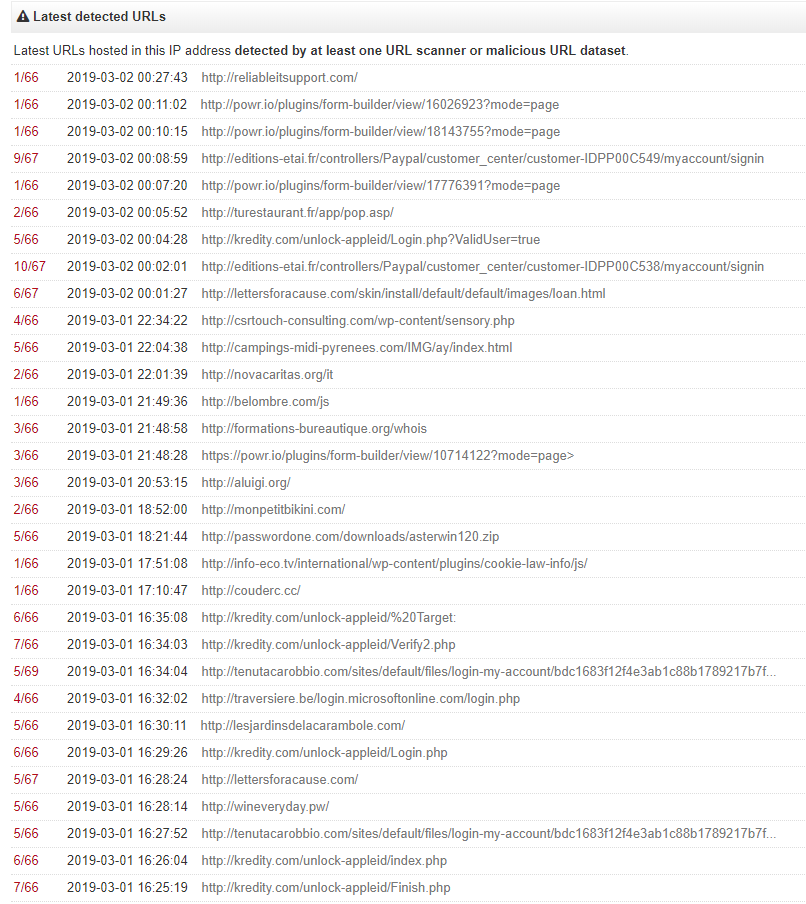
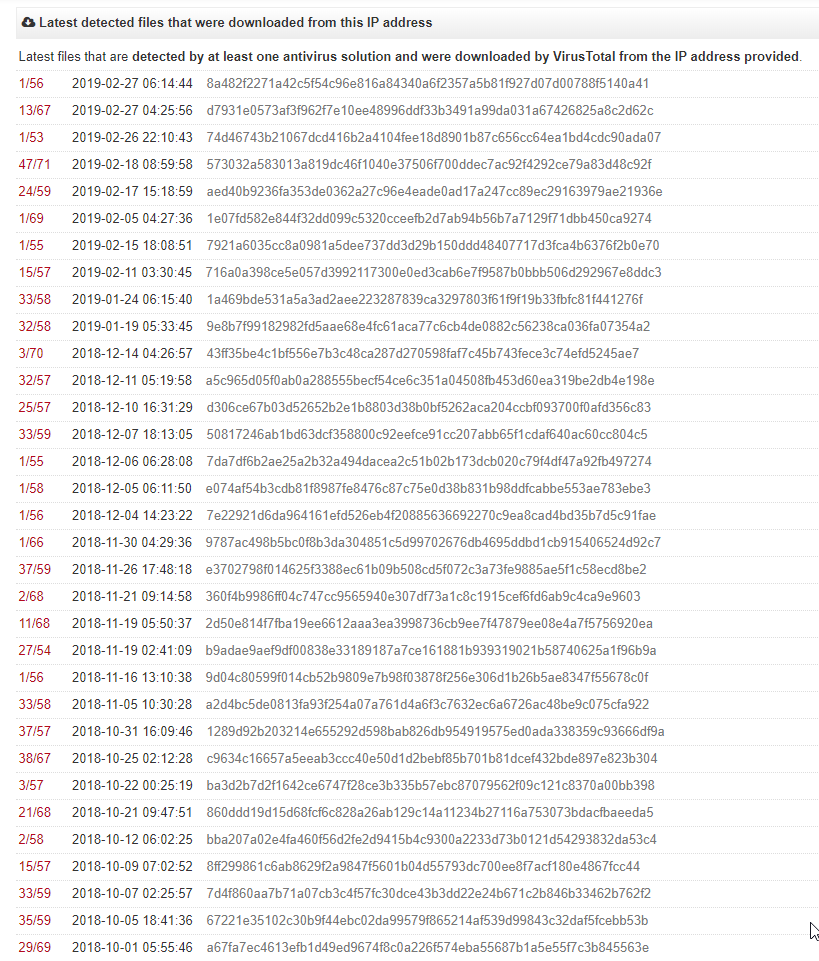
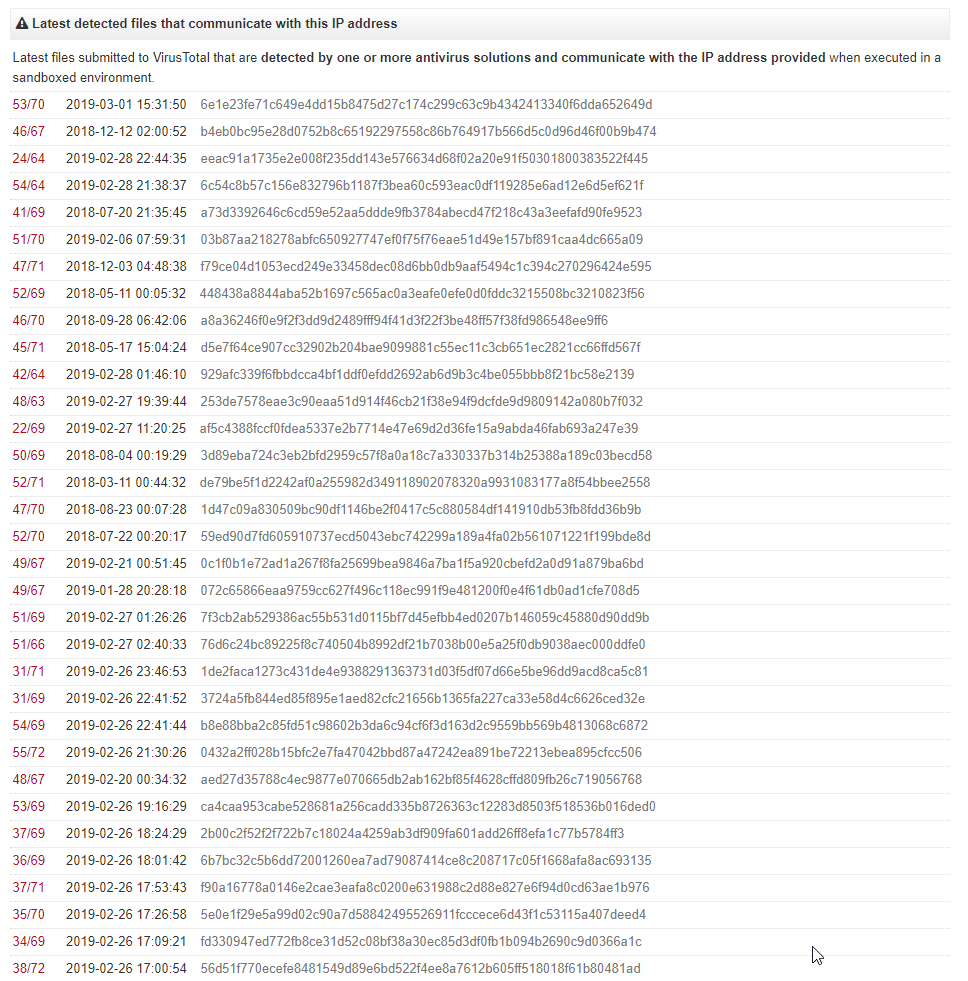
We conducted some other searches and found that this IP was associated with various malicious content including the Locky Ransomware, windows (PE) executables, etc.
IBMcloud https://exchange.xforce.ibmcloud.com/ip/217.70.184.38
Alienvault: https://otx.alienvault.com/indicator/ip/217.70.184.38
Maltiverse: https://www.maltiverse.com/sample/1e1f31686600bd9b83bc8b37713f67cec3931978e8b883e5f0396aaa18726f7b
It is very possible that our research means nothing, but because there seems to be an association between the domain and the IP addresses we found, we assume there is a chance (even the smallest) that there is some sort of campaign that could be run, at some point. Note, we didn’t have much to go on other than the basic info that was available in the forum posts that have been circulating around. Curiosity got the best of us and we wanted to see what we could uncover.
Happy hunting!



