This vulnerability was responsibly disclosed to Axcient/Anchor on November 4, 2019.
Affected versions: > 2.7.1.1498
During a penetration test we came across a file sharing application called SynedTool. When performing some of the more simpler tests we identified that this application is vulnerable to an Information Leakage and Improper Error Handling vulnerability.
The application allows for enumeration of legitimate user accounts. This was identified by examining the log in errors. When what appeared to be an invalid username was tried, only the error message “Your username or password is incorrect” was displayed. If what appeared to be a valid user account was tried, the error messages “Invalid Credentials” and “Your username or password is incorrect” would be displayed. You can see examples of this in the screenshots below.
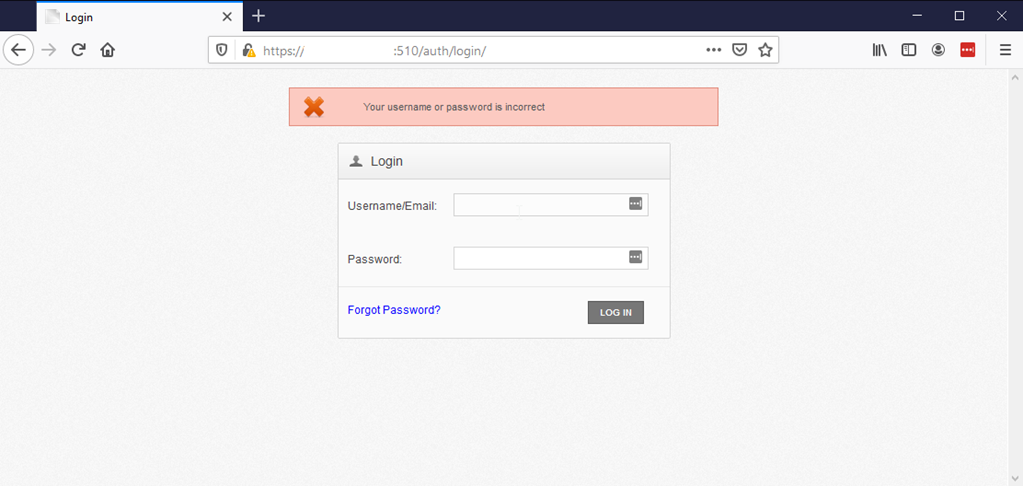
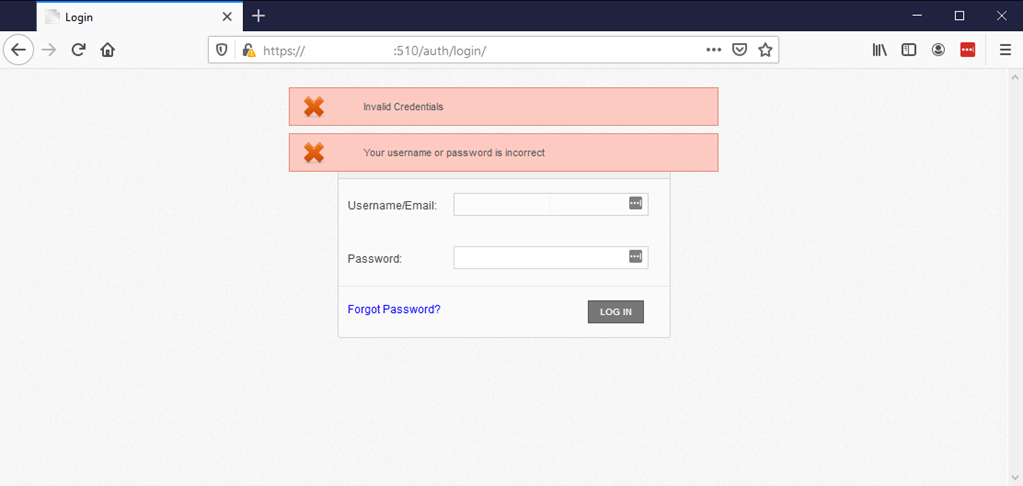
The application also allows for unlimited authentication attempts, so one can use a combination of user lists to identify all valid users and wordlists to potentially identify accounts with brute force attacks. We leveraged a python script to enumerate the user accounts for our particular client but avoided performing any brute force attempts since this wasn’t in scope.
During the test we identified that version 2.7.1.1498 was affected by this vulnerability. It also appears that all prior versions are also affected. Like any responsible penetration tester would do we notified Axcient of our finding and their response was:
Thanks for bringing this to our attention, we actually do have a fixed ready for this coming in a future build of the server, but I’ve gone ahead and linked this ticket up to the task with our development team. For the time being I’ll be escalating the ticket up to one of my senior colleagues to hold onto, we’ll reach back out once the fix has been released.
Since notifying them there appears to have been a new release but no mention of a fix. Available here: https://support.efolder.net/hc/en-us/articles/360038991953-Anchor-Web-Portal-2-7-2-Release-Notes



